WordPress Hacking Statistics (How Many Websites Get Hacked?)
Want to find out how many WordPress websites get hacked? Then you won’t want to miss these WordPress hacking statistics!
WordPress is the most popular CMS in the world. It powers more websites than any other software. WordPress is used by over 800 million websites worldwide. But unfortunately, that popularity also makes it one of the most common targets for hackers.
Every year, millions of WordPress websites fall victim to cyberattacks. If you don’t want to be part of that group, it helps to stay informed.
With that in mind, we will share over 50 WordPress hacking statistics that website owners and admins need to know this year.
The stats below will help you learn more about WordPress security’s current state in 2023. They’ll reveal the most common website vulnerabilities that hackers exploit, and highlight some best practices that can help you keep your website safe and secure.
Ready? Let’s get started!
How many WordPress websites get hacked?
Nobody knows exactly how many WordPress websites get hacked, but our best estimate is at least 13,000 per day. That’s around 9 per minute, 390,000 per month, and 4.7 million per year.
We arrived at this estimation because Sophos reports that over 30,000 websites are hacked daily, and 43% of all websites are built on WordPress.
What percentage of WordPress websites get hacked?
According to Sucuri, 4.3% of WordPress websites scanned with SiteCheck (a popular website security scanner) in 2022 had been hacked (infected). That’s around 1 in every 25 websites.
While not every WordPress website will use SiteCheck, this is probably a good indication of the percentage of total WordPress websites that get hacked.
Sucuri also found that 10.4% of WordPress websites were at risk of getting hacked as they ran out-of-date software.
What’s the most commonly-hacked CMS platform?
WordPress was the most commonly-hacked CMS (content management system) in 2022, according to Sucuri’s annual hacked website report. Over 95.6% of infections detected by Sucuri were on websites running WordPress.
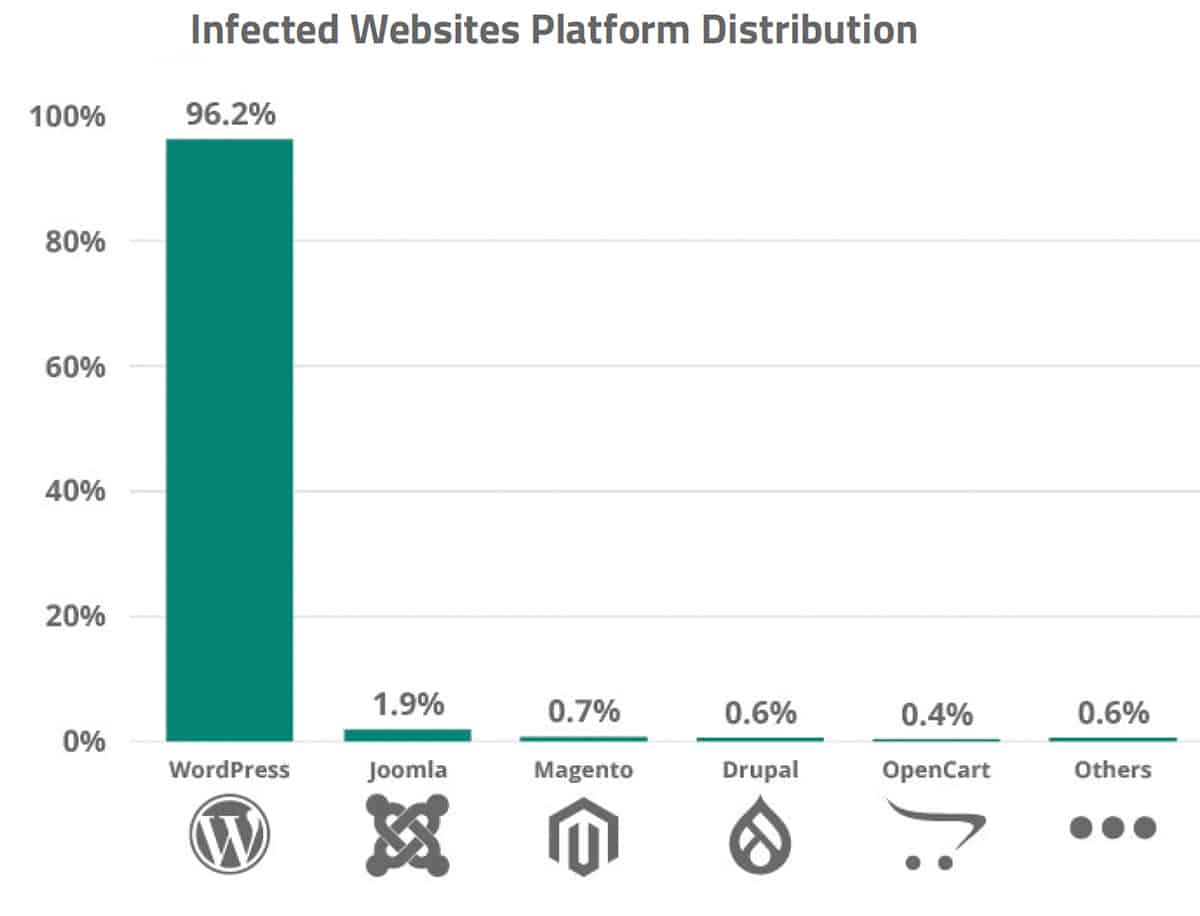
Top 5 most-hacked CMS:
- WordPress – 96.2%
- Joomla – 1.90%
- Magento – 0.70%
- Drupal – 0.60%
- OpenCart – 0.40%
However, it’s worth noting that the fact that most infections detected by Sucuri were on WordPress websites doesn’t necessarily mean there’s something inherently vulnerable about the WordPress core software.
On the contrary, it’s more likely to simply reflect that WordPress is by far the most commonly used CMS, and that WordPress users are more likely to use plugins like Sucuri than users of other CMS software.
Sources: Sophos, Colorlib, Sucuri1
What are the most common WordPress hacks?
Malware is the most common type of WordPress hack seen by Sucuri during incident response. In total, 61.65% of the infections found by Sucuri were categorized as malware. Other common infections included backdoor hacks, SEO spam, hacktools, and phishing hacks.
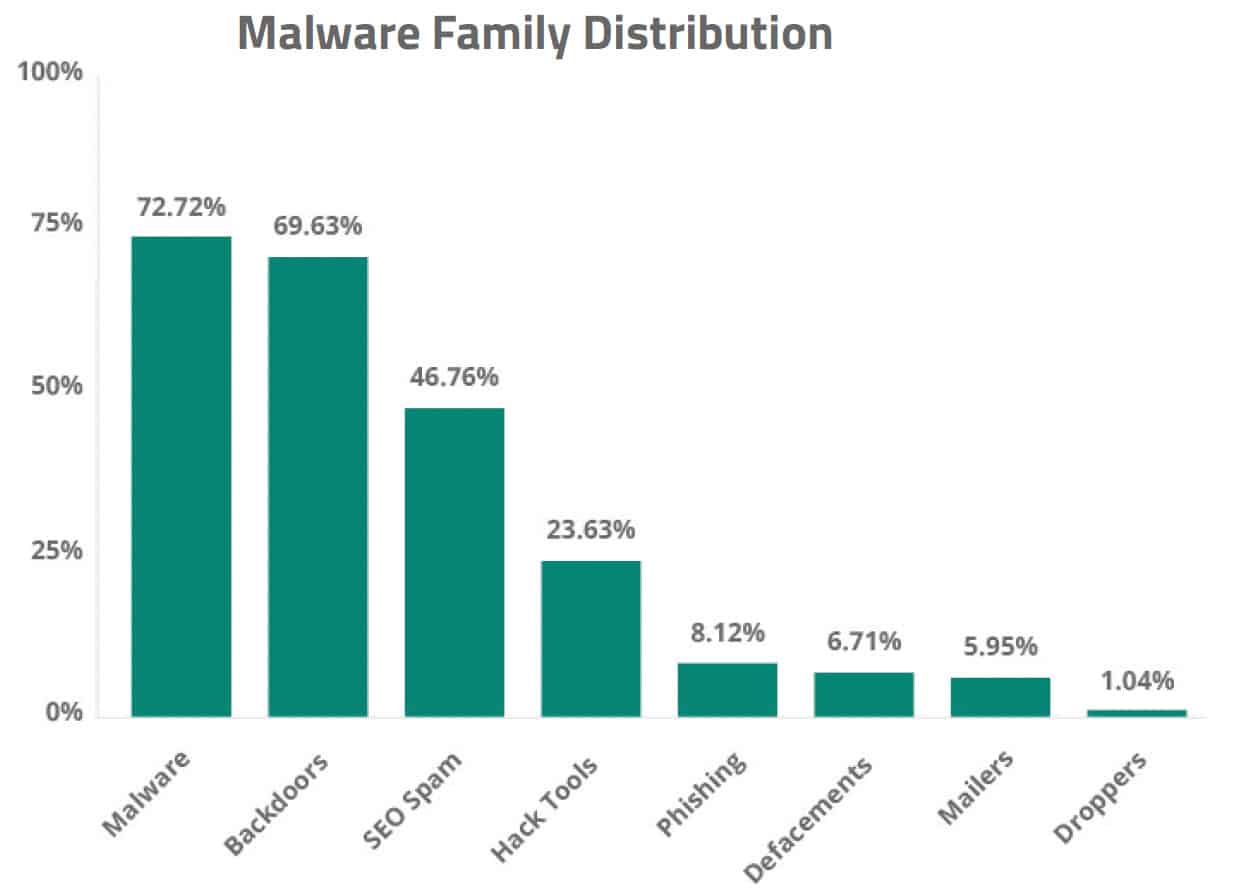
Top WordPress hacks found by Sucuri
- Malware 72.72%
- Backdoor – 69.63%
- SEO Spam – 46.76%
- Hack Tool – 23.63%
- Phishing – 8.12%
- Defacements – 6.71%
- Mailer – 5.95%
- Dropper – 1.04%
Malware
Malware is the most common type of WordPress hack found by Sucuri. This is a broad, catch-all term that refers to any kind of malicious software used by cybercriminals to harm or exploit your WordPress website. The most common type of malware is PHP malware.

Malware is one of the most damaging security infections as, unlike backdoors and SEO spam, it often puts your site visitors at risk of malicious action.
For example, one common example of malware is a SiteURL/HomeURL infection, which involves infecting your site with code that redirects your visitors to malicious or scam domains to steal their login details.
Another example is credit card skimming: a web-based attack in which hackers inject malicious code onto ecommerce websites to steal visitors’ credit and debit card information. Interestingly, stats show that 34.5% of websites infected with a credit card skimmer run on WordPress.
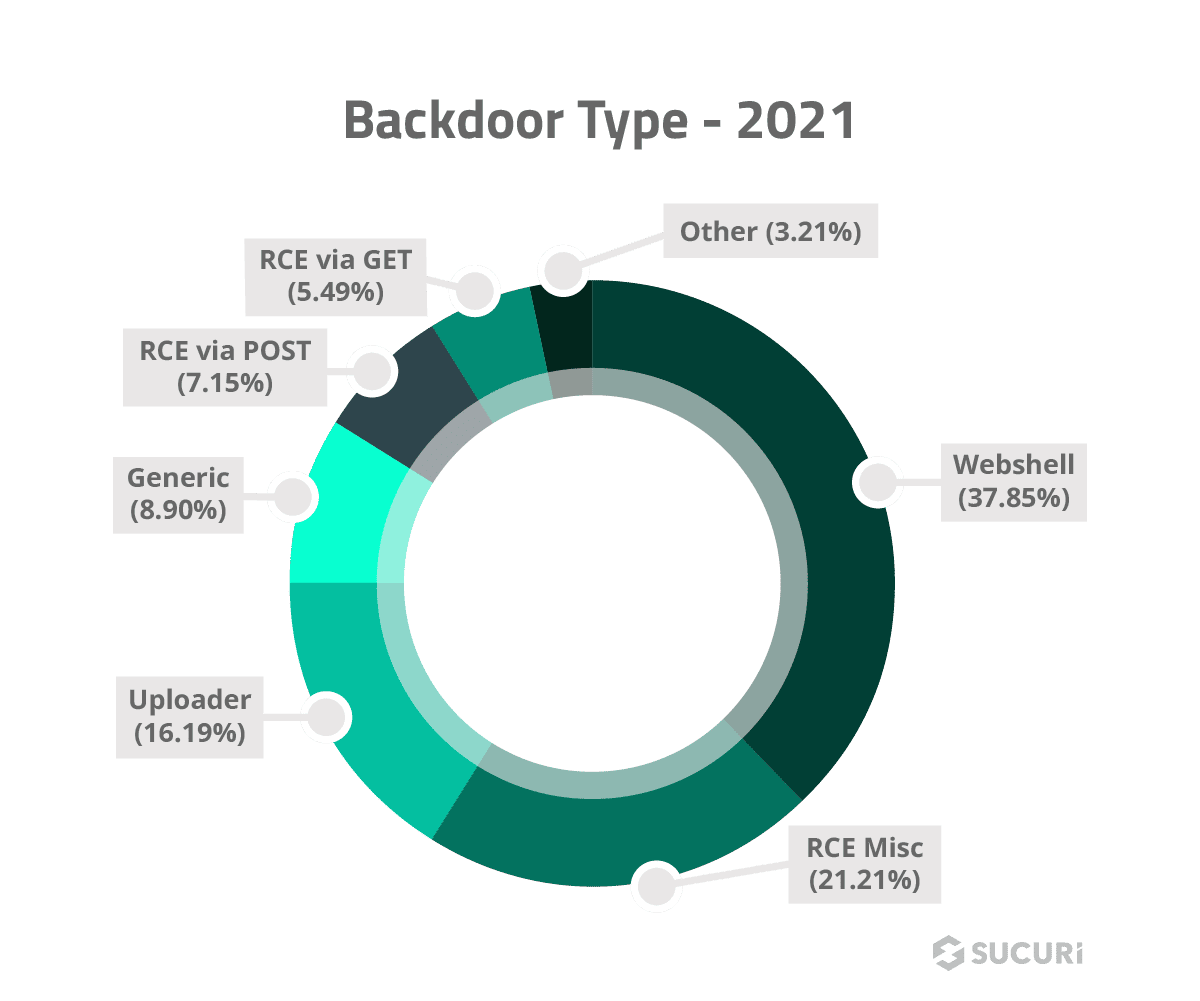
Backdoor
Backdoors are the second most common type of WordPress hack found by Sucuri. As the name suggests, these types of infections allow hackers to bypass the usual login channels in order to access the backend of your website via a secret ‘backdoor’ and compromise the environment.
SEO spam
SEO spam is the third most common hack found by Sucuri and is present in over half of all infections.
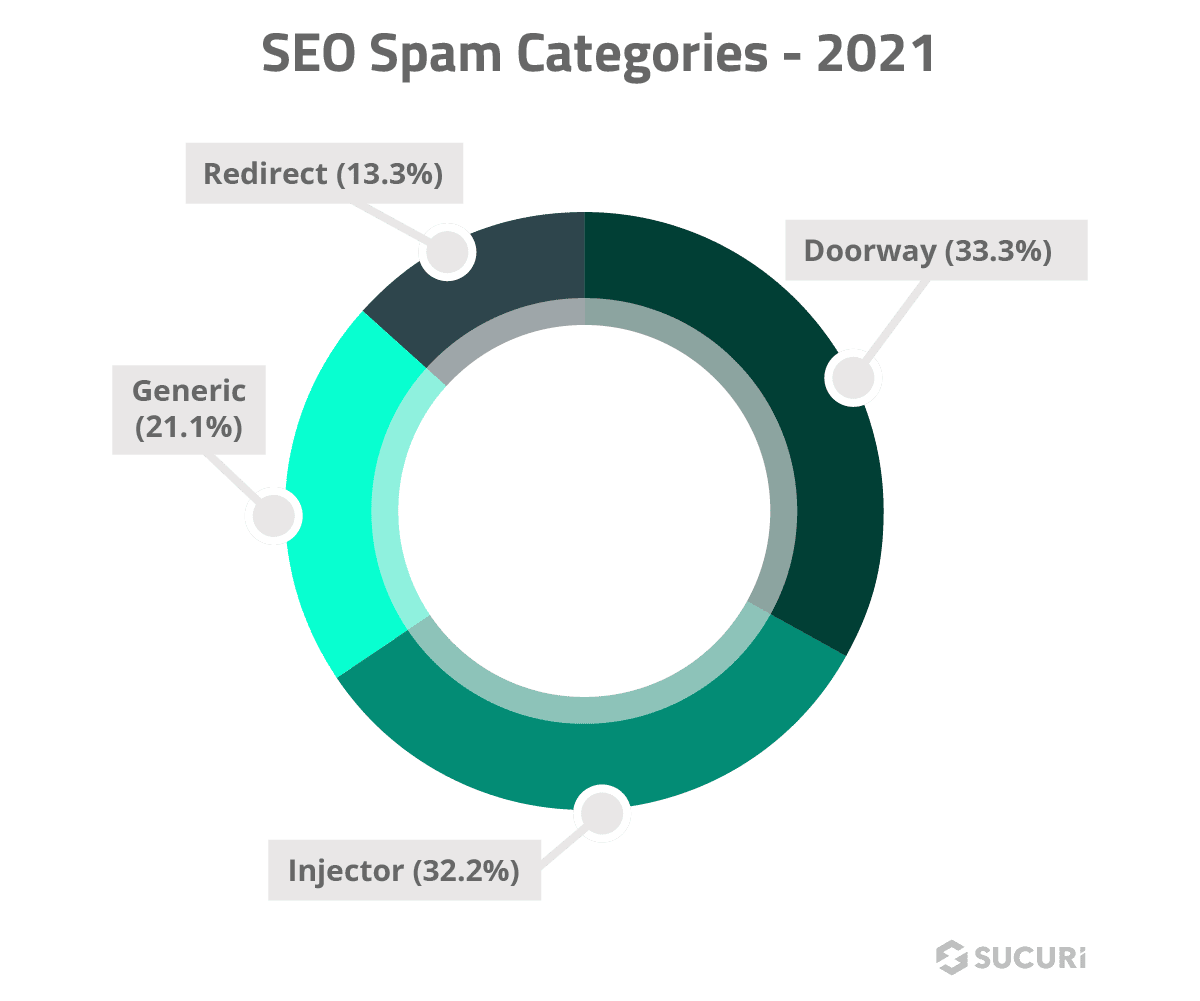
This type of hack involves infecting sites to improve the search engine optimization of and direct traffic to third-party websites by setting up redirects, publishing spam posts, and inserting links.
Meanwhile, this damages your domain’s SEO score and can negatively impact your organic ranking in search engines like Google.
Key statistics:
- 32.2% of SEO spam infections relate to spam injectors, which pepper the compromised environment with hidden spam links for SEO purposes.
- Other types post a ton of blogs for SEO purposes, usually on spammy topics.
- 28% of SEO Spam infections relate to pharmaceuticals (Viagra, Cialis, etc.)
- 22% were related to Japanese SEO Spam (these campaigns pollute the victim’s website search results with knock-off designer goods and appear in the SERPs in Japanese text.
- Redirect campaigns most often point to .ga and .ta top-level domains
Sources: Sucuri1
WordPress security vulnerabilities
Next, let’s look at some WordPress statistics that tell us more about the security vulnerabilities hackers most often exploit.
What’s the biggest WordPress security vulnerability?
Themes and plugins are the biggest WordPress security vulnerabilities. 99.42% of all security vulnerabilities in the WordPress ecosystem came from these components in 2021. That’s up from 96.22% in 2020.
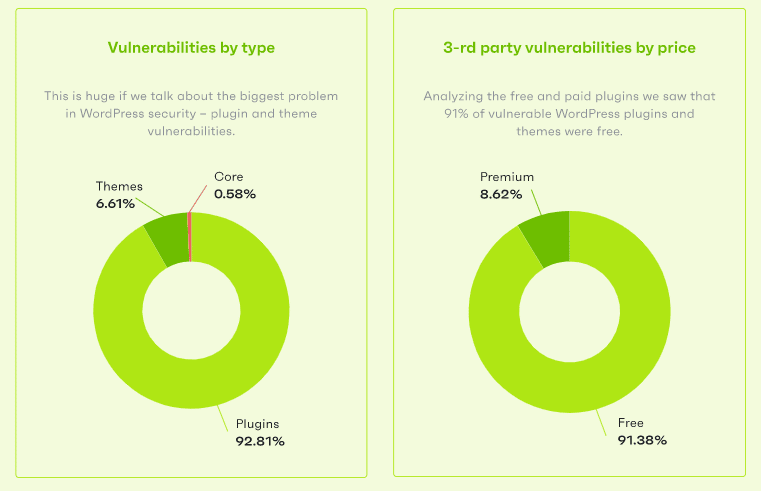
To break that down a bit further, 92.81% of vulnerabilities came from plugins, and 6.61% from themes.
Amongst vulnerable WordPress plugins, 91.38% were free plugins available through the WordPress.org repository, and just 8.62% were premium plugins sold through third-party marketplaces like Envato.
Key statistics:
- 42% of WordPress sites have at least one vulnerable component installed.
- Interestingly, only 0.58% of security vulnerabilities found by Patchstack originated from the core WordPress software.
Top WordPress vulnerabilities by type
Cross-site scripting vulnerabilities (CSS) make up almost half (~50%) of all the vulnerabilities added to Patchstack’s database in 2022. This is up from 36% in 2020.
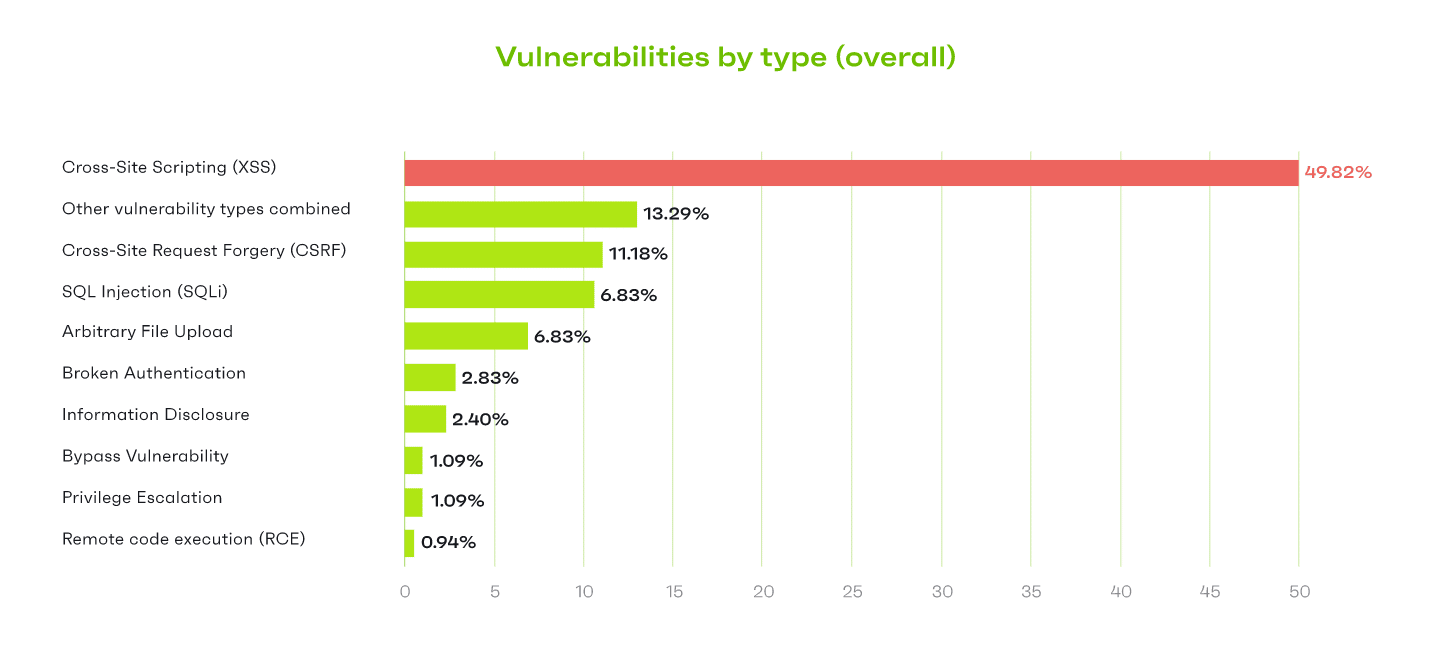
Other common vulnerabilities in the database include:
- Other vulnerability types combined – 13.3%
- Cross-site Request Forgery (CSRF) – 11.2%
- SQL Injection (SQLi) – 6.8%
- Arbitrary File Upload – 6.8%
- Broken Authentication – 2.8%
- Information disclosure – 2.4%
- Bypass Vulnerability – 1.1%
- Privilege Escalation – 1.1%
- Remote Code Execution (RCE) – 0.9%
Top WordPress vulnerabilities by severity
Patchstack ranks each vulnerability in its database according to its severity. It uses the CVSS system (Common Vulnerability Scoring System) to do so, which assigns a numerical value between 0 and 10 to each vulnerability based on its severity.
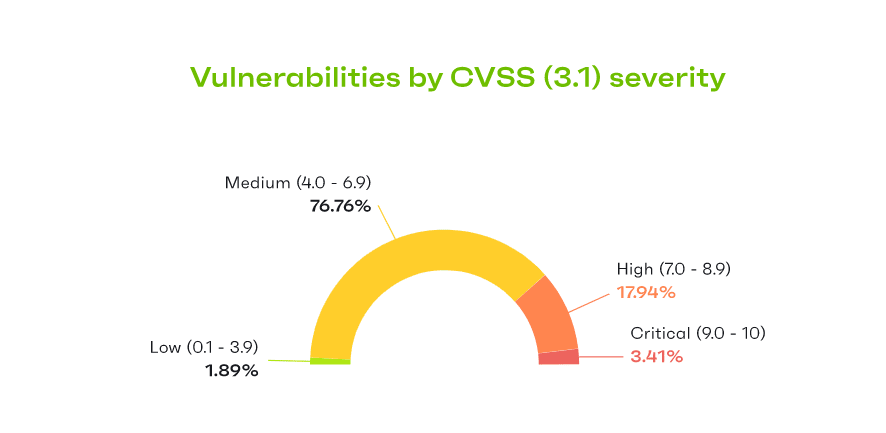
Most of the WordPress vulnerabilities identified by Patchstack last year received a CVSS score between 4 and 6.9, which makes them ‘Medium’ severity.
- 3.4% of identified vulnerabilities were Critical severity (9-10 CVSS score)
- 17.9% of identified vulnerabilities were High severity (7-8.9 CVSS score)
- 76.8% of identified vulnerabilities were Medium severity (4-6.9 CVSS score)
- 1.9% of identified vulnerabilities were Low severity (0.1-3.9 CVSS score)
Top attacked vulnerabilities
The top four ‘attacked’ vulnerabilities in Patchstack’s database were:
- OptinMonster (version 2.7.4 and earlier) – Unprotected REST-API to Sensitive Information Disclosure and Unauthorized API access
- PublishPress Capabilities (version 2.3 and earlier) – Unauthenticated Settings Change
- Booster for WooCommerce (version 5.4.3 and earlier) – Authentication Bypass
- Image Hover Effects Ultimate (version 9.6.1 and earlier) – Unauthenticated Arbitrary Options Update
Source: Sucuri1, Patchstack
WordPress plugin hacking statistics
As we mentioned earlier, WordPress plugins are the most common source of security vulnerabilities that allow hackers to infiltrate or compromise your website. Next, we’ll look at some WordPress hacking statistics that relate to WordPress plugins.
In case you didn’t know, plugins are small third-party software applications that you can install and activate on your WordPress site to extend its functionality.
How many WordPress plugin vulnerabilities are there?
There were 35 critical vulnerabilities found in WordPress plugins in 2022. Worryingly, two were in plugins with over 1 million installations: All in One SEO and WP Fastest Cache.

The good news is that the plugin developers promptly patched the above vulnerabilities. However, 29% of the WordPress plugins found to have critical vulnerabilities didn’t receive a patch.
What are the most vulnerable WordPress plugins?
Contact Form 7 was the most commonly-identified vulnerable WordPress plugin. It was found in 36.3% of all infected websites at the point of infection.
However, it’s important to point out that this doesn’t necessarily mean Contact Form 7 was the attack vector that the hackers exploited in these instances, only that it contributed to the overall insecure environment.
TimThumb was the second most commonly-identified vulnerable WordPress plugin at the point of infection and was found in 8.2% of all infected websites. This is especially surprising given that the TimThumb vulnerability is over a decade old.
Top 10 identified vulnerable WordPress plugins:
| Top Vulnerable WordPress Components | Percentage |
|---|---|
| 1. Contact Form 7 | 36.3% |
| 2. TimThumb (image resizing script used by themes and plugins) | 8.2% |
| 3. WooCommerce | 7.8% |
| 4. Ninja Forms | 6.1% |
| 5. Yoast SEO | 3.7% |
| 6. Elementor | 3.7% |
| 7. Freemius Library | 3.7% |
| 8. PageBuilder | 2.7% |
| 9. File Manager | 2.5% |
| 10. WooCommerce Block | 2.5% |
WooCommerce accounts for 7.8% of all hacked websites, and that’s significant because it is an eCommerce platform. For more information, please read in-dept WooCommerce statistics.
How many WordPress plugins should you have?
Best practices suggest website owners and admins should have as few WordPress plugins as possible. The fewer plugins you have, the lower your risk of encountering a vulnerability.
The average WordPress site has 18 different plugins and themes installed. This is 5 less than last year and seems to be a move in the right direction on the surface.
However, more of those plugins and themes were outdated this year compared to last year. On average, 6 out of 18 plugins installed on websites were outdated, compared to just 4 out of 23 last year.
What is the most popular WordPress security plugin?
Jetpack is the most popular WordPress security plugin on the WordPress plugin directory, with over 5 million downloads. However, it’s debatable whether or not Jetpack can be classed as a true security plugin.
Although it includes security features like 2FA, malware detection, and Brute Force protection, it also includes other features for things like speed optimization, analytics, and design tools. This makes it more of an all-in-one plugin than a security plugin.
Regarding dedicated security plugins, Wordfence is the most popular, with 4 million downloads on the WordPress plugin database.
WordPress theme vulnerabilities
12.4% of WordPress theme vulnerabilities identified by Patchstack had a critical CVSS score (9.0 – 10.0). And worryingly, 10 themes had a CVSS 10.0 security risk that compromises the user’s entire site via an unauthenticated arbitrary file upload and option deletion.
Sources: Patchstack, WordPress1, WordPress2
How can you protect your WordPress website from being hacked?
You can protect your WordPress website from being hacked by reducing your use of plugins and themes, making sure you update all software frequently and patch identified vulnerabilities, and through WordPress hardening.
Here are some statistics that reveal more about increasing the security of your WordPress website.
Most common WordPress hardening recommendations
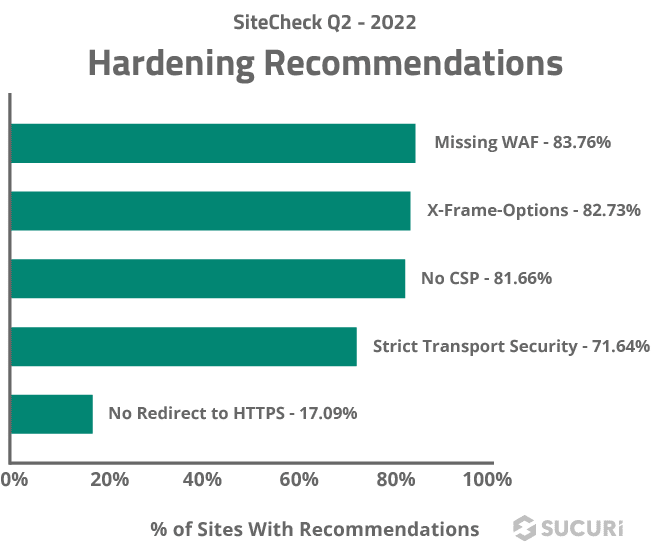
According to data from Sucuri, over 84% of websites didn’t have a website application firewall (WAF), making this the top WordPress hardening recommendation.
WAFs help virtually patch known vulnerabilities and safeguard your site against DDoS attacks, comment spam, and bad bots.
83% of websites were also found to be missing X-Frame-Options—a security header that helps improve your security by protecting you from clickjacking and preventing hackers from embedding your website onto another through an iframe. This makes X-Frame-Options the second most common hardening recommendation.
Top 5 most common hardening recommendations detected by Sucuri:
- Missing WAF – 84%
- X-Frame options – 83%
- No CSP – 82%
- Strict Transport Security – 72%
- No Redirect to HTTPS – 17%
How do website admins protect their sites?
According to a survey of website admins and owners, 82% have undertaken security hardening, a practice that involves taking steps to make your WordPress site more difficult to hack.
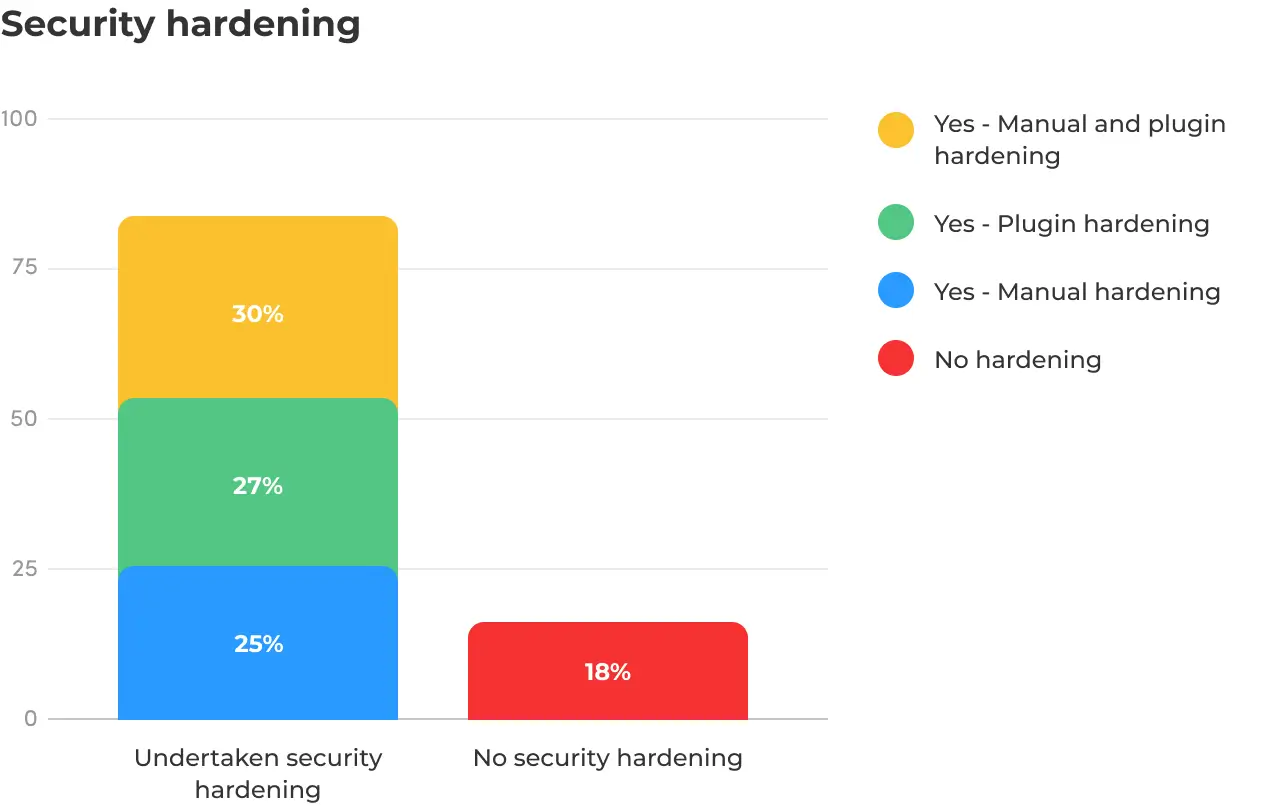
Of those, 27% used a plugin to harden their site, 25% undertook manual hardening, and 30% did a combination of both. Only 18% didn’t do any hardening at all.
Key statistics:
- 81% of surveyed WordPress admins have at least one firewall plugin installed
- 64% of surveyed WordPress admins use 2FA (Two-factor authentication), while 36% don’t
- 65% of surveyed WordPress admins use activity log plugins.
- 96% of surveyed WordPress administrators and website owners view WordPress security as very important. And 4% view it as somewhat important
- 43% of admins spend 1-3 hours per month on WordPress security
- 35% of admins spend over 3 hours per month on WordPress security
- 22% of admins spend less than 1 hour on WordPress security.
How do web professionals secure their clients’ sites?
According to a recent survey, almost half of all web professionals that work with clients rely on premium security plugins to secure their clients’ websites:
Top methods web professionals use to secure client sites:
- 45.6% pay for premium security plugins
- 42.4% use free security plugins
- 31.2% pay a professional security provider
- 28.8% handle security issues in-house
- 24.8% refer their clients to a professional security provider
- 10.4% use other methods
- 6.4% tell their clients to use free plugins
- 5.6% don’t have a plan for website security
Top security tasks web professionals perform
Updating WordPress (or whatever CMS the client uses) and plugins is the most common security task performed by web professionals, with three-quarters of all survey respondents saying this is something they do.
Top tasks web security professionals carry out for their clients:
- 75% update CMS and plugins
- 67% backup sites
- 57% install SSL certificates
- 56% monitor or scan websites for malware
- 38% fix sites related to security issues
- 34% patch vulnerabilities
How often should you update your WordPress site?
As we mentioned earlier, keeping your WordPress website is updated is incredibly important from a security standpoint.
Most site managers update their website on a weekly basis (35%), but 20% run updates daily, and 18% do so monthly. 21% of site managers have some kind of automatic updates configured so they don’t have to do it manually.
Key statistics:
- 52% of surveyed WP owners and admins have auto-updates enabled for WP software, plugins, and themes.
- 25% always test updates in a test or staging environment first
- 32% sometimes test updates
- 17% never test updates
- 26% only test major updates
Sources: Sucuri2, Sucuri3, WP White Security
The costs of WordPress hacking
Getting hacked can cost businesses a small fortune. Removing malware professionally costs $613 on average, but it can cost thousands—or even millions—of dollars more to recover from a serious data breach.
Aside from monetary costs, WordPress hacking can also indirectly affect cost businesses money by impacting revenues and damaging brand reputation.
How much does it cost to fix a hacked WordPress website?
WordPress malware removal costs $613, but that can vary substantially from case to case. Individually, prices ranged from $50 up to $4,800.
In comparison, paying for website security to protect your site from malware costs an average of $8 per site/month—making it a no-brainer for most site owners.
How much do data breaches cost businesses?
Hacking is responsible for 45% of data breaches worldwide. And on average, the average cost of a data breach is $3.86 million. But of course, this varies based on the organization’s size, industry, etc.

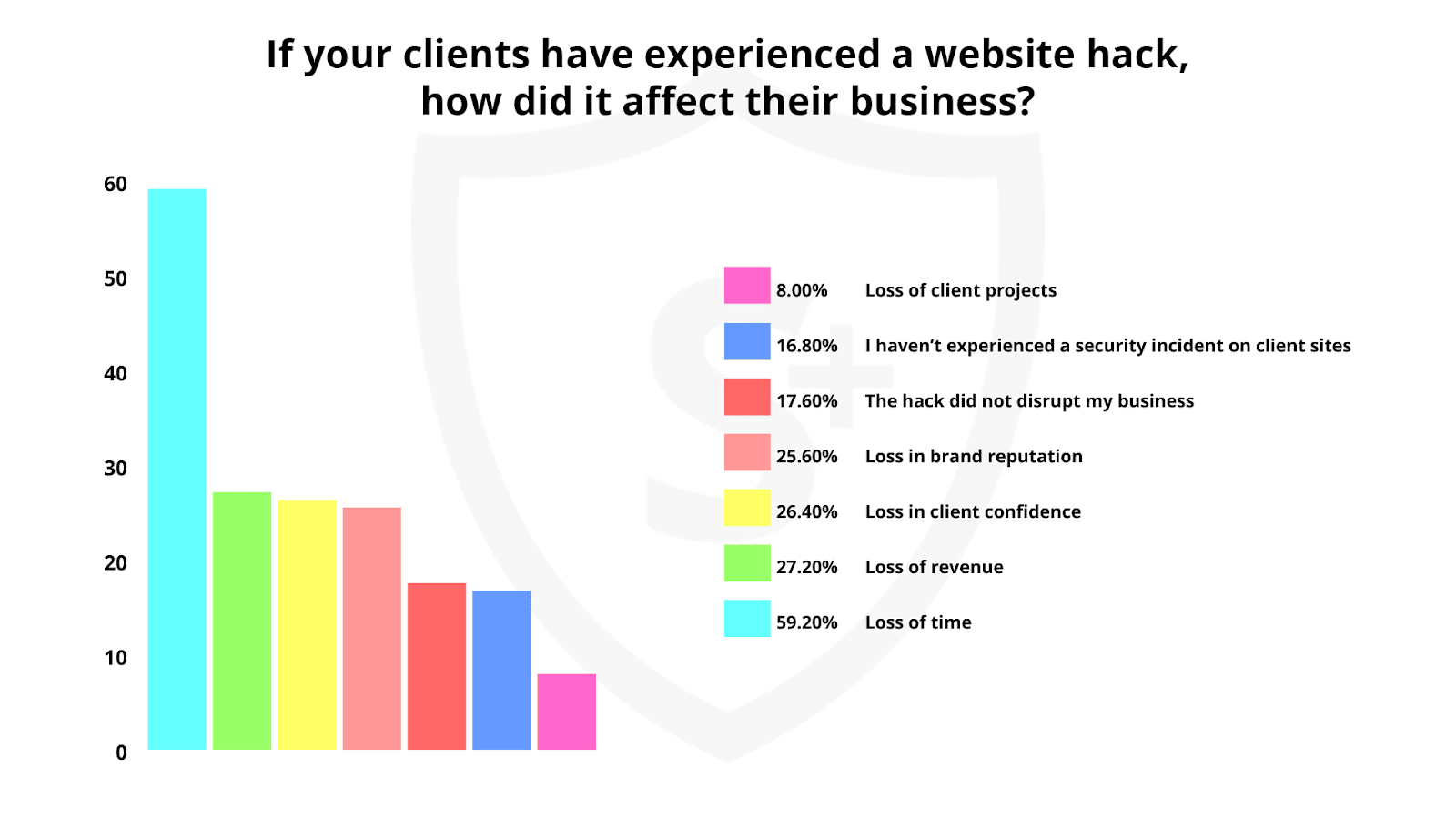
What are the biggest impacts of WordPress hacking?
According to surveyed web professionals, the greatest impact of a hack on their client’s business was a loss of time (59.2%). Other negative impacts include:
- Loss of revenue – 27.2%
- Loss in client confidence – 26.4%
- Loss in brand reputation – 25.6%
- No disruption – 17.6%
Sources: Patchstack, Statista, Sucuri3
What’s the most secure version of WordPress?
The most secure version of WordPress is always the latest version. At the time of writing, this is WordPress 6.0.2.
How often does WordPress release security updates?
WordPress typically releases several security and maintenance updates every year. There were 4 in 2021. The latest security release (at the time of writing) was WordPress 6.0.2, which fixed three security issues: an XSS vulnerability, an output escaping issue, and a possible SQL injection.
Are old versions of WordPress easily hacked?
Only 50.3% of WordPress websites were found to be out of date when infected, which suggests running an out-of-date version of the WordPress software only roughly correlates with infection. Nonetheless, best practices suggest you should always use the latest version of WordPress to minimize your risk of getting hacked.
Sources: Sucuri1, WordPress3
Final thoughts
That concludes our roundup of the most important WordPress hacking statistics for 2023. We hope you found this data useful!
If you want to learn even more about WordPress, check out our roundup of WordPress statistics.
You can also learn more about how to protect your site from hackers by reading our in-depth guide on how to improve WordPress security.
Good luck!







Hi! I’m looking into having a website built for my business and all of the companies I’ve spoken to, except one, have said WordPress is the way to go for best SEO. The one company advising against WordPress sent me this article and said WordPress makes businesses too vulnerable so they don’t create on WordPress. In your opinion, which platform is best for SEO for a small service based company that doesn’t sell products online. Ty!
Renee,
WordPress is as safe as a popular CMS can be. Yes, many WordPress websites go get hacked but that’s because 810 million websites use it, so even a tiny percentage of websites means that millions of website get hacked.
However, we have too look into main reasons why WordPress websites get hacked and the main one is that people use user name “admin” and a simple password reused on many other websites and other online accounts. Just changing a user name to anything other than “admin” will protect your website fro majority of attacks.
Another of top reasons is using an outdated version of WordPress core, plugins and themes. Updating these things takes seconds and can be automated so WordPress does all the updates for you. With these simple things out of the way, there is slim to no chance that your website will ever get hacked.
Of course, make sure to have at least a daily backups (automated), so if ever happens you can fix everything within few hours. Here are the best WordPress backup solutions that you can use or just use a WordPress hosting that offers backups as part of their service.